-
Notifications
You must be signed in to change notification settings - Fork 435
Dynamic filtering: quick guide
Dynamic filtering pane (available only in Advanced Mode):
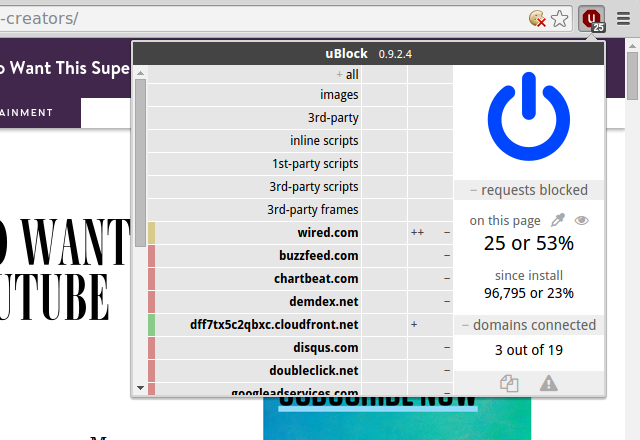
Static filtering refers to the filters which comes from the filter lists, i.e. EasyList, EasyPrivacy, hpHosts, etc. Dynamic filtering are those filtering rules which have an air of firewall rules.
First column: what is to be dynamically filtered:
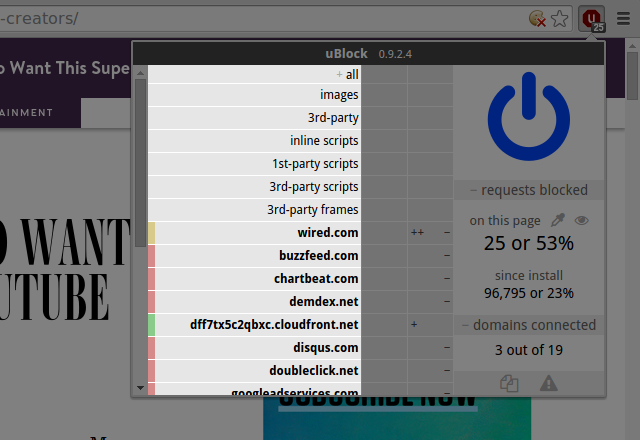
As you can see, you can create dynamic filtering rules for object types, or hostnames according to their origin.
The color of an entry indicate whether all requests were blocked (reddish), all requests were allowed (greenish), or some were blocked some were allowed (yellowish).
In bold, domain names. Domain names are hostnames, but hostnames are not necessarily domain names from uBlock's point of view: domain names are extracted as per Mozilla Public Suffix list.
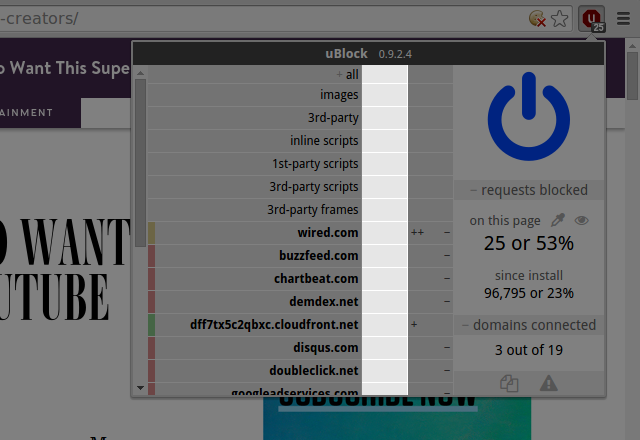
Second column: global dynamic filtering rules, i.e. whatever rule appears in this column applies everywhere, on all sites:
Third column: local dynamic filtering rules, i.e. whatever rule appears in this column applies to the current site only:
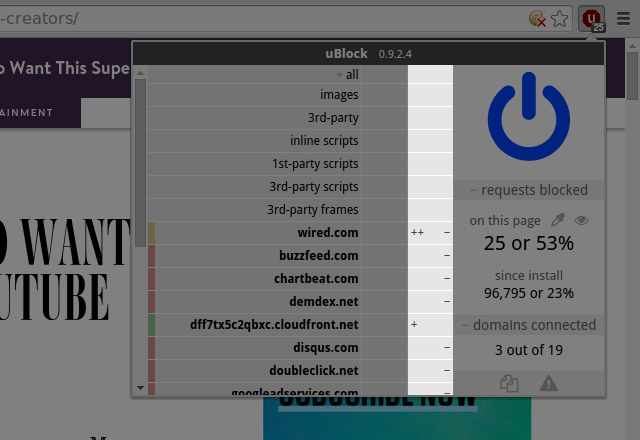
The cells in the third column gives an overview of how many requests were blocked/allowed:
-
-or+= between 1-9 network requests were blocked or allowed, respectively -
--or++= between 10-99 network requests were blocked or allowed, respectively -
---or+++= 100 or more network requests were blocked or allowed, respectively - blank cell = no network requests occurred for the specific hostname
So there are global dynamic filtering rules, and local dynamic filtering rules.
Sensible security- and privacy-wise: blocking all 3rd-party frames by default everywhere:
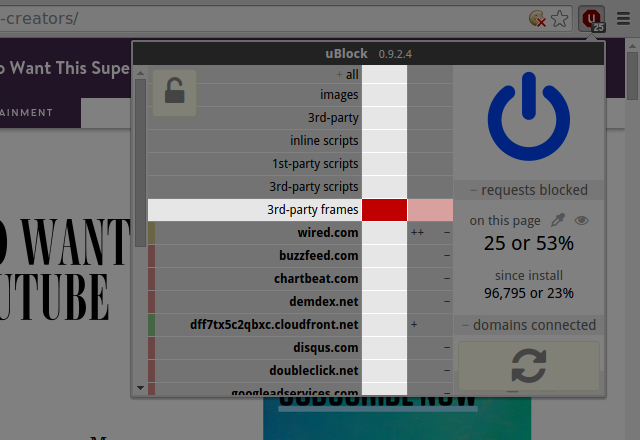
Dynamic filtering overrides static filtering. This means a block dynamic rule will override any existing allow static filters. This means you can block with 100% certainty using dynamic filtering rules. Similarly, an allow dynamic filtering rule will override any existing block static filters, i.e. you can allow with 100% certainty with dynamic filtering (useful to un-break sites broken by some static filters).
Update: With the addition of strict filtering, the above is no longer accurate. Dynamic filters will not override a strictly filtered host or domain.
All embedded 3rd-party frames were blocked on the page. Good. However it appears there was an embedded Youtube video in the article:
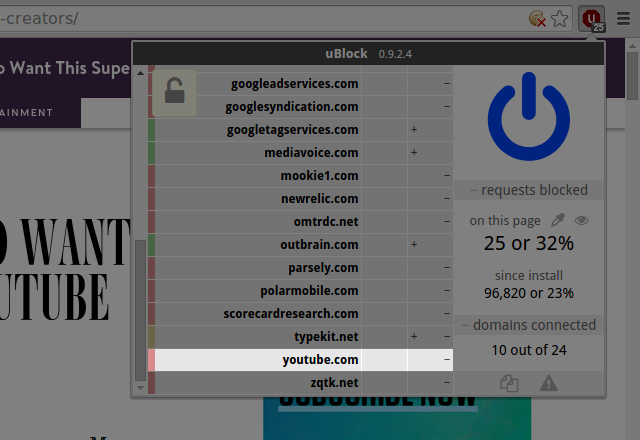
If you want to block all 3rd-party frames by default, except for embedded Youtube videos on that particular site, two solutions.
Create a local noop rule for 3rd-party frames:
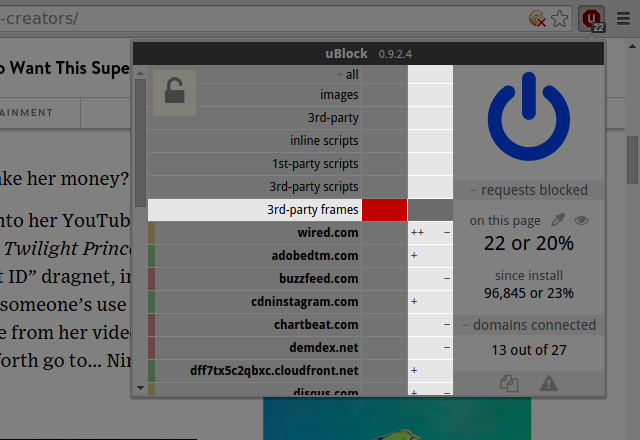
It works, the embedded Youtube video can now be played.
However the above rule would result in all 3rd-party frames on the site to be unblocked. Not so good.
Create a local noop rule for youtube.com:
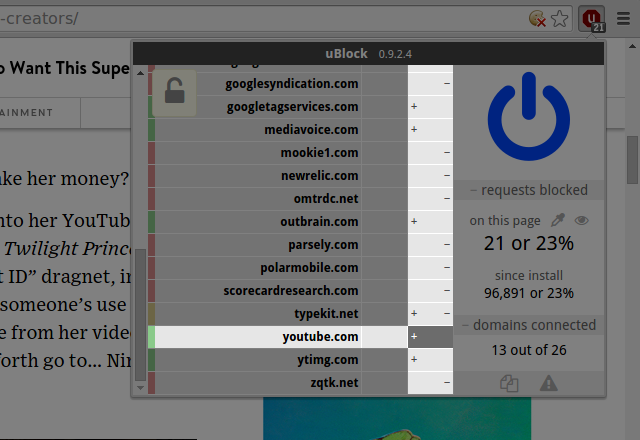
This will prevent dynamic filtering rules to apply to anything from youtube.com, but only on that site.
Remember that noop rules bypass only broader dynamic filtering rules; static filtering is left completely intact, which means you won't see ads in the embedded Youtube videos.
What if you want to block 3rd-party frames everywhere by default, but want whatever embedded Youtube video to not be blocked by default on any site?
It is just a matter of creating a global noop rule for youtube.com:
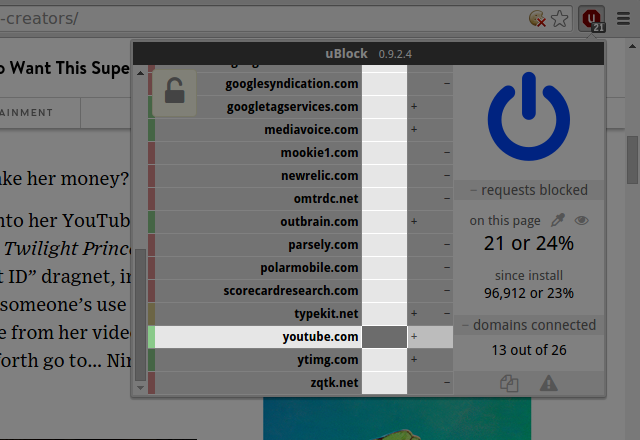
Which means: do not apply any dynamically filtering rule to youtube.com by default (i.e. everywhere).
Local dynamic filtering rules override global ones.
In other words: More specific dynamic filtering rules override less specific ones. For example, dynamic filtering rules for youtube.com (specific) override dynamic filtering rules for 3rd-party frames (generic).
All dynamic rules are temporary by default: Click the padlock icon to persist the ruleset for a specific web site.
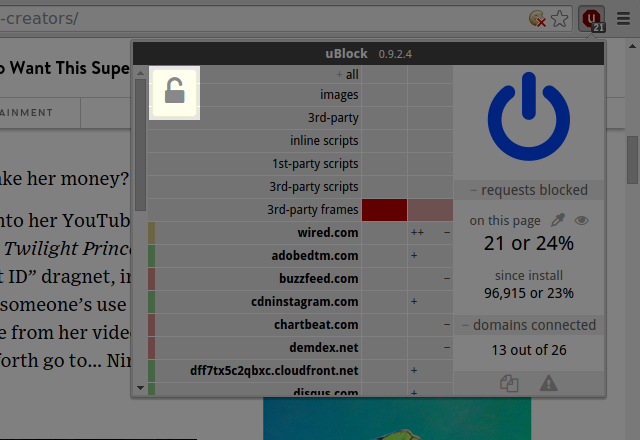
- The padlock icon will be visible if and only if there is at least one temporary rule in the pane
- This is the optimal way to use dynamic filtering, as using this feature is often a matter of trial and error
- This prevents ruleset pollution: your ruleset will be only those rules which you will have explicitly persisted
- If you Ctrl-click to set/unset a rule, it will be immediately persisted (command ⌘-click on Mac)
We covered the block and noop dynamic filtering rules. What about the allow rule?
The dynamic filtering allow rule is most useful to un-break sites broken by some static filters.
Someone found out Boldchat site was broken when using uBlock:
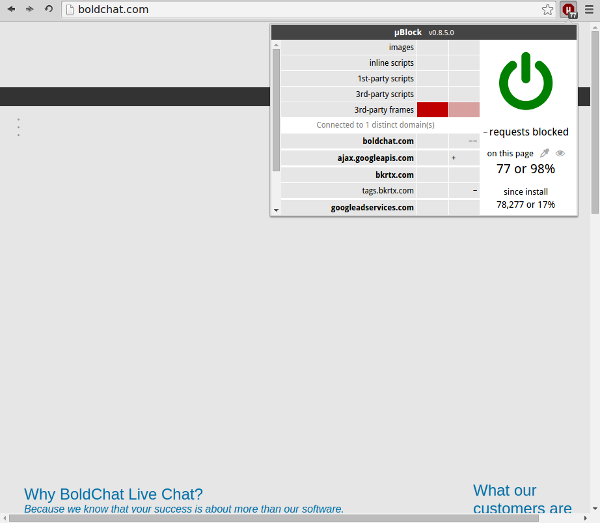
The content of the dynamic filtering pane makes it clear that there is a static filter somewhere blocking network requests to boldchat.com. It turned out there was static filter boldchat.com in "Peter Lowe's Ad Server" list.
Using a local allow dynamic filtering rule fixes the breakage:
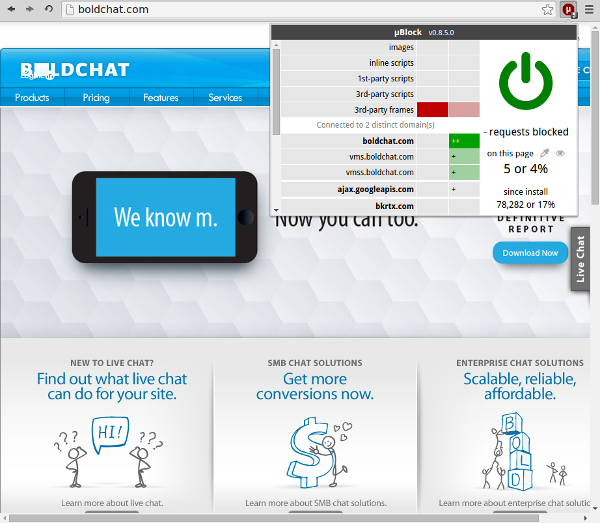
It is easier for a user to point-and-click for a quick fix then to actually craft an exception static filter like @@||boldchat.com$~third-party and force a reload of all static filters (which results in significant memory churning).
Another example of un-breaking a site.
Typically, use only narrow allow dynamic filtering rules to un-break sites. These allow rules override static filters, so if you add an unnecessarily broad allow dynamic filtering rule, you could allow in ads/trackers/annoyances.
More: Take control of your privacy in your own hands (will move this here eventually)