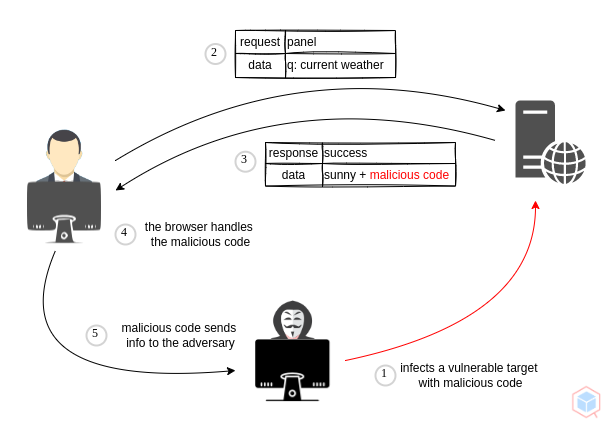
A threat actor may inject malicious content where content is saved into a database, when users visit the malicious vulnerable website, the malicious content is loaded from the database and the browser executes that.
- Threat actor infects a vulnerable target with malicious code to a victim
- The victim requests the vulnerable target and receives the malicious code
- When malicious code gets executed, it calls back the threat actor
Vary
- Read & modify data
- Output encoding
- Browser built-in XSS preveiton
cb251c97-067d-4f13-8195-4f918273f41b