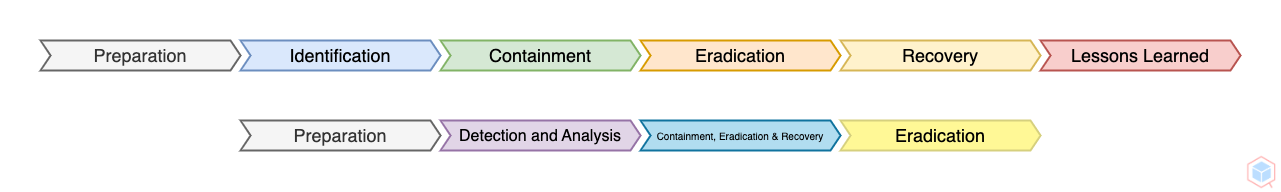
Incident response is a set of steps that are used to handle the aftermath of a data breach or cyberattack
This step determines how the origination will respond in case a data breach or cyberattack occurs (It's established before the incident)
- List of assets (Risk assessment)
- Communication
- Documentation
- Training
- IR plan
Determinate whether a data breach or cyberattack happened or not
Once an incident is identified, then affected assets are isolated
- Short-term
- Long-Term
Eliminate the cause of the data breach or cyberattack
Bring the affected assets back to production and monitor them to ensure everything is back to normal
Finish up documentation and answer some follow-up questions regarding how to improve the current process
51a6dc04-1550-4e08-a1e9-f4e909959b4f