> 🔒 A simple Node.js API that connects to MongoDB,
generates and throws back a JWT Token to the final endpoint
What's Authentication and Authorization • What is JWT • Project Requirements •
How to: Run this project locally • API's provided • Screenshots
Made with ❤️ by João Vitor Lessa - 👏🏻 Get in Touch!
Hit the ⭐️ button if you like this project!
Authentication and authorization are used in security, particularly when it comes to getting access to a system. Yet, there is a significant distinction between gaining entry into a house (authentication) and what you can do while inside (authorization).
Authentication is the process of verifying a user’s identification through the acquisition of credentials and using those credentials to confirm the user’s identity. The authorization process begins if the credentials are legitimate. The authorization process always follows the authentication procedure.
You were already aware of the authentication process because we all do it daily, whether at work (logging into your computer) or at home (logging into a website). Yet, the truth is that most “things” connected to the Internet require you to prove your identity by providing credentials.
Authorization is the process of allowing authenticated users access to resources by determining whether they have system access permissions. By giving or denying specific licenses to an authenticated user, authorization enables you to control access privileges.
So, authorization occurs after the system authenticates your identity, granting you complete access to resources such as information, files, databases, funds, places, and anything else. That said, authorization affects your capacity to access the system and the extent to which you can do so.
JSON Web Tokens (JWT) are an RFC 7519 open industry standard for representing claims between two parties. For example, you can use jwt.io to decode, verify, and produce JWT.
JWT specifies a compact and self-contained method for communicating information as a JSON object between two parties. Because it is signed, this information can be checked and trusted. JWTs can be signed using a secret (using the HMAC algorithm) or an RSA or ECDSA public/private key combination. In a moment, we’ll see some examples of how to use them.
- Node.js installed
- MongoDB Cluster connection
- Navigate to the
appfolder - In the file
.env, insert your MongoDB database credentials - Run:
npm install - Run:
node server.js - Open the address:
http://localhost:4001to test the API calls
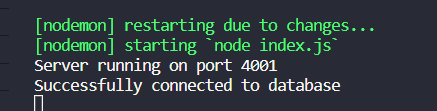
- The server and the database should be running without any crashing
- Check the image below:
| Method | URL | Actions |
|---|---|---|
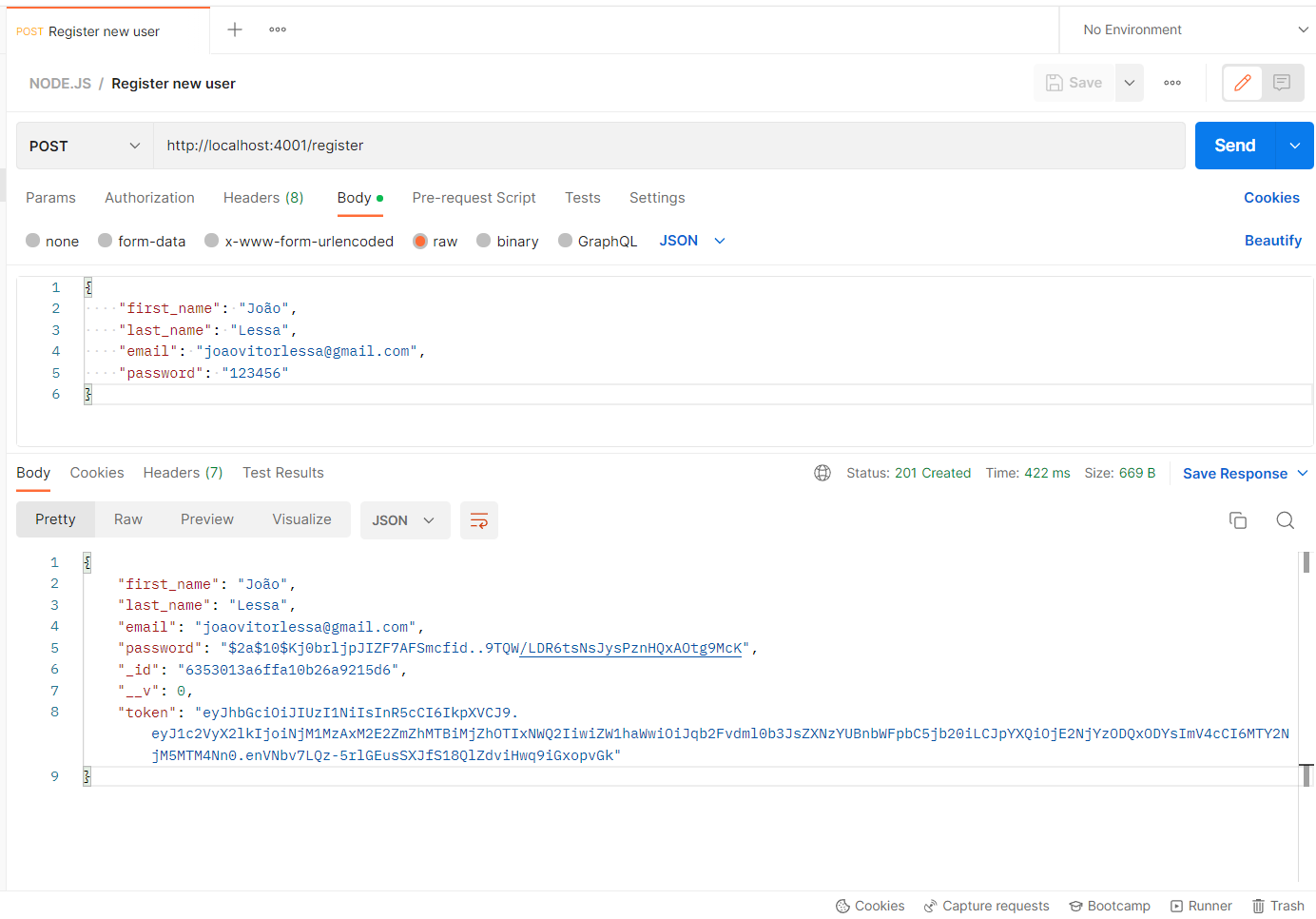
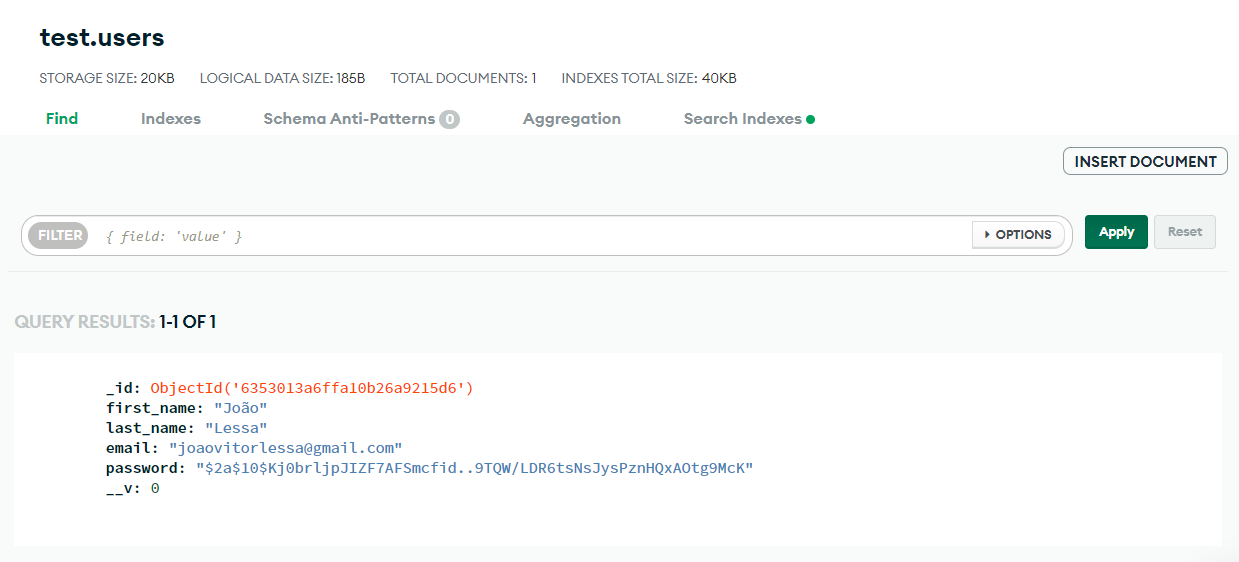
| POST | http://localhost:4001/register | Signup new account |
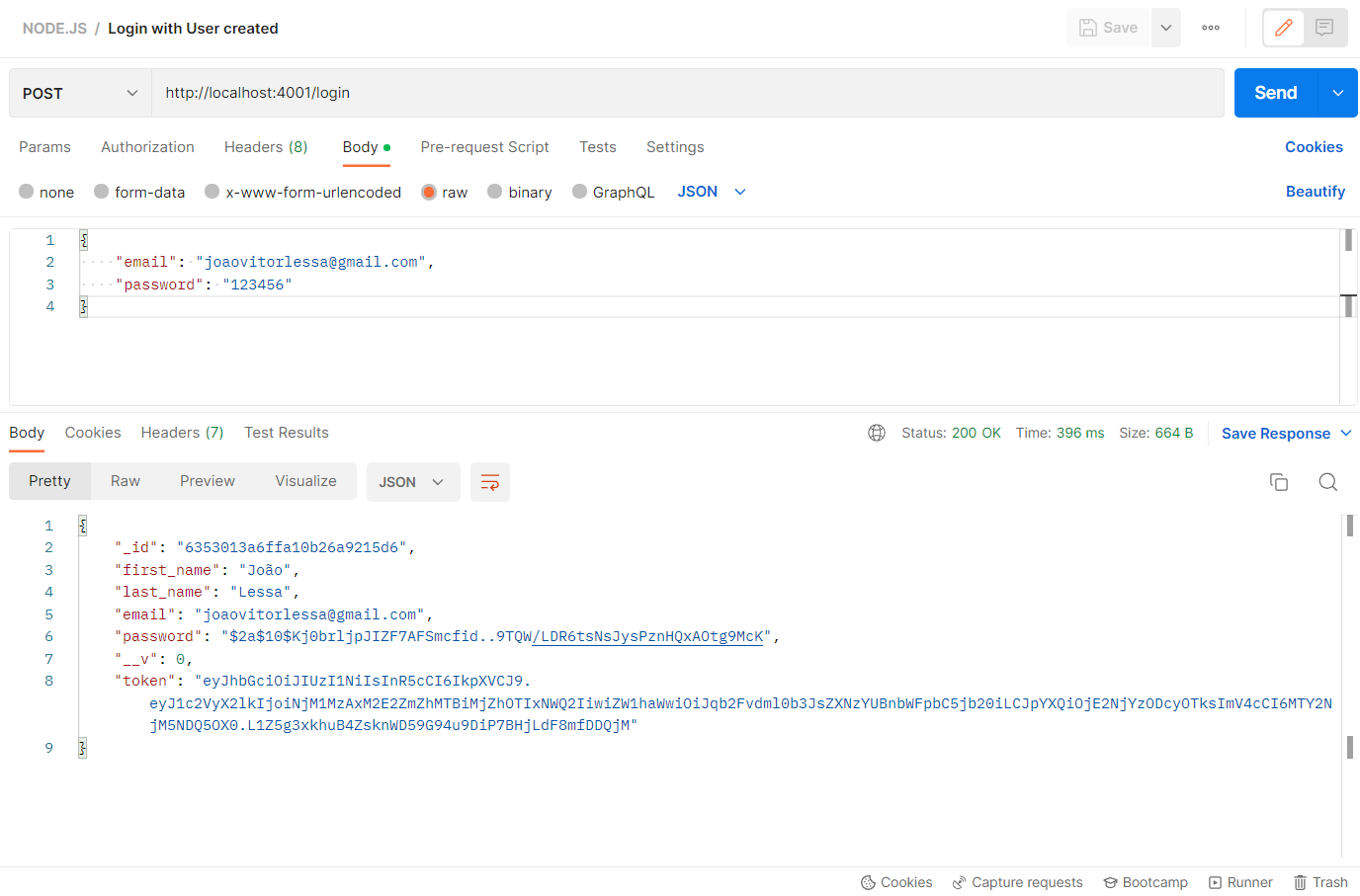
| POST | http://localhost:4001/login | Login an account |
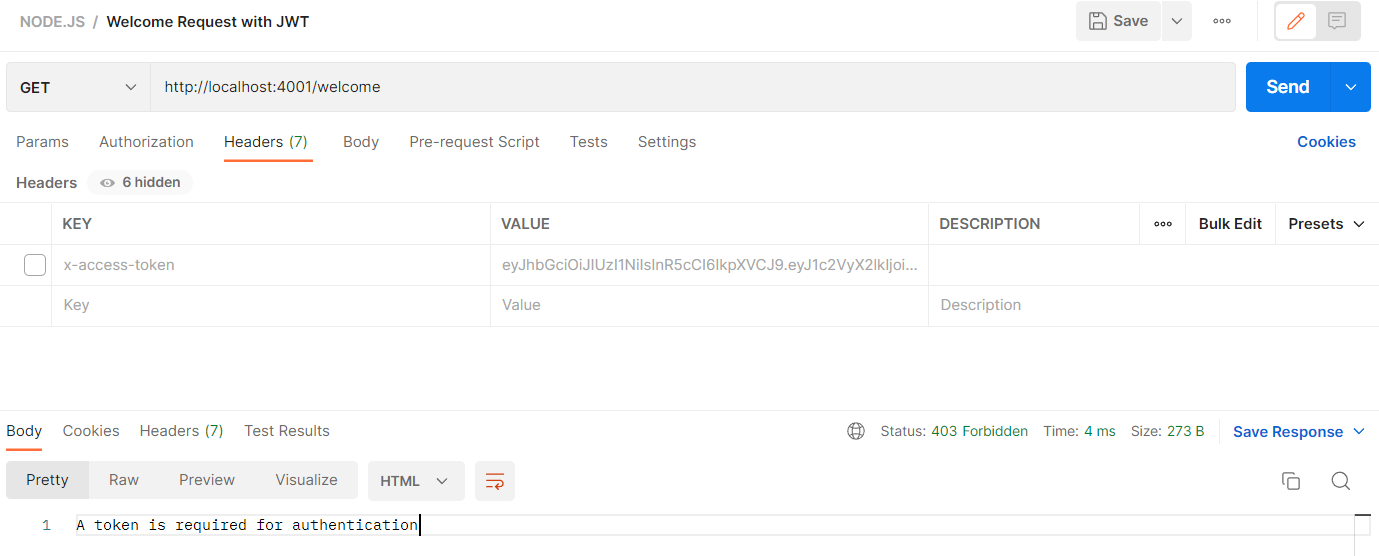
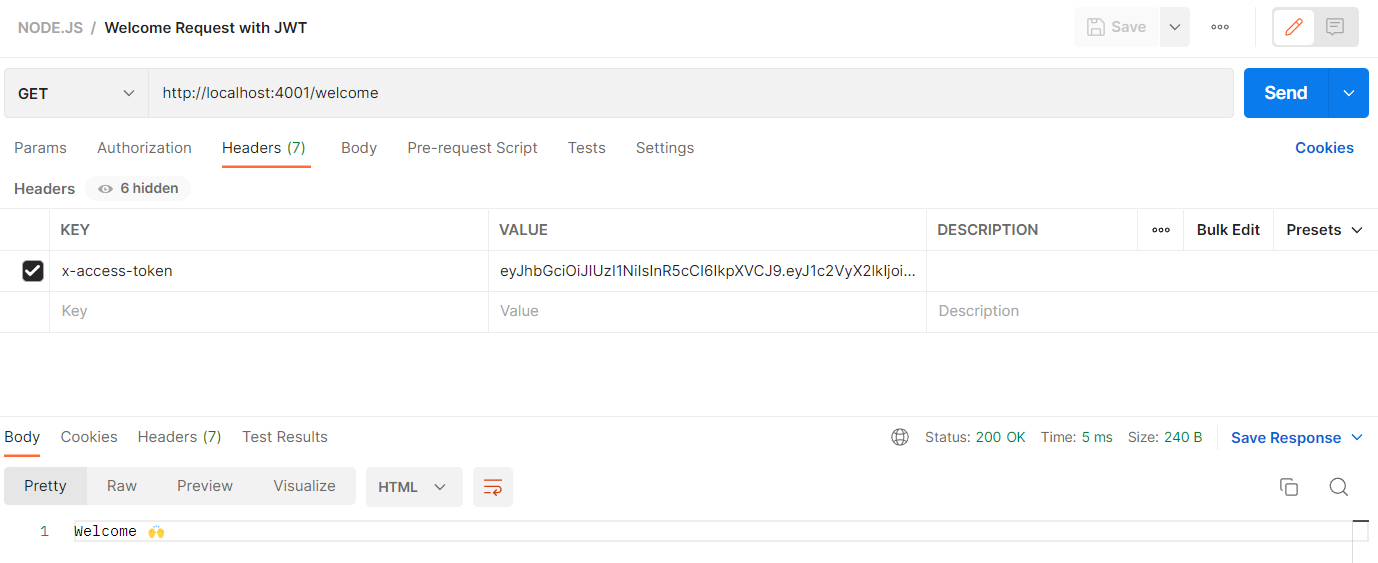
| GET | http://localhost:4001/welcome | Welcome Request Testing JWT |