- Basics of Frida
- Dynamic Binary Instrumentatation
- Common Challenges while pentesting Android
- Modes of operation
- Frida Installation
- Frida Common Api for Android
- Frida Hooking
- Frida Python Binding
- References
- Setting up the Frida
- Learn Basic Frida Commands
- Reverse Enginnering and Bypassing the apps
- Dynamic binary instrumentation tool
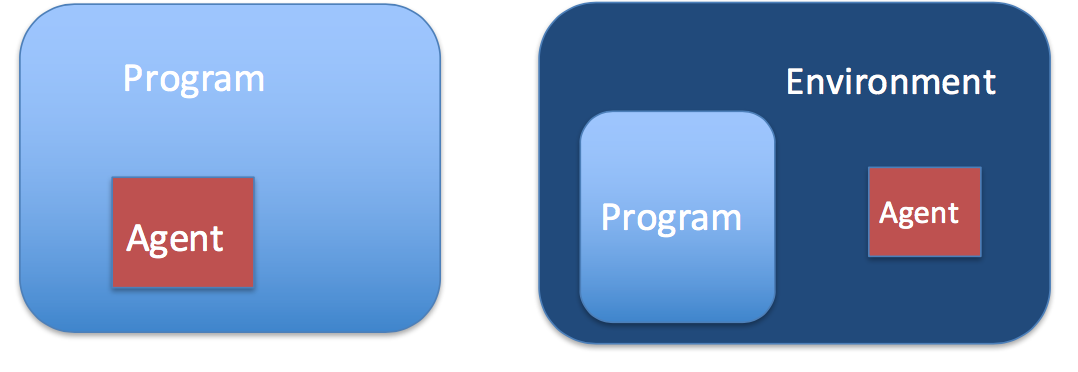
Types of Dynamic Instrumentation
-
Injected
-
Embeded
How we change the app logic ?
- Root Bypassing
- Anti Debugging
- Anti Emulation
- Bypassing App Logic
- spawn an existing process
- hook to the running program
- Requires the root access
- Frida-gadget a shared library
- Using a dynamic linker feature like LD_PRELOAD or DYLD_INSERT_LIBRARIES
- Not used in android
pip install frida
pip install frida-tools
adb push frida-server /data/local/tmp/
adb shell "chmod 755 /data/local/tmp/frida-server"
adb shell "/data/local/tmp/frida-server &"
The tool to check the running process
To check the running process inside the emulator
frida-ps -U - To check the running apps inside the emulator
frida-ps -Ua - To check the running apps inside the emulator
frida-ps -Uai - To check the running app process inside the emulator
This tool help to list the devices
frida-ls-devices
The cli version of frida
frida -U <process-name>
frida -U -f <process-name>
frida -U -f <process-name> --no-pause
- Java.perform - call the function
- Java.use-use the particular class
var main = Java.use("sg.vantagepoint.root.MainActivity");
- .implementation-override the existing function main.isDeviceRooted.implementation
- .overload-to use polymorphism .overload(“datatype”).implementation
Java.perform(function() {
var main = Java.use("sg.vantagepoint.root.MainActivity");
main.function-name.implementation = function() {
console.log("In function A");
return false;
}
});frida -U -f --no-pause -l l1.js
import frida, sys
ss = """
Java.perform(function () {
//logic goes here
"""
device = frida.get_usb_device()
pid = device.spawn(["sg.vantagepoint.root"])
session = device.attach(pid)
script = session.create_script(ss)
script.load()
device.resume(pid)
raw_input()
python filename.py